Simplify Threat Detection and Response with SureMDM and SIEM Integration
dec 27, 2024 | Nareddy Saivikas Reddy
Imagine this: It's a seemingly ordinary day at your organization until a sudden and devastating cyberattack strikes your IT infrastructure. Sensitive data is compromised, systems are disrupted, and your organization’s reputation takes a hit. The result is severe financial losses, legal issues, and a loss of customer trust.
Hard to imagine, right? However, this could happen to any business that doesn't streamline threat detection and improve incident response. This is where Security Information and Event Management (SIEM) comes into play.
If you have questions like - What exactly is SIEM, and how does it help businesses identify and manage security risks in real-time? And why should you integrate SIEM tools with Mobile Device Management (MDM) solutions?
Read this blog further to get the answers.
What is SIEM?
Security Information and Event Management (SIEM) refers to a set of tools and services that provide real-time analysis of security alerts generated by applications, network hardware, devices, and users. SIEM platforms gather, analyze, and store log data to help organizations detect and respond to security threats and incidents promptly.
What Types of Cyberattacks Can SIEM Solutions Detect?
SIEM tools are known for their ability to provide visibility into the IT infrastructure and can help detect various types of cybersecurity threats, like
- Insider Threats: Security vulnerabilities or attacks that arise from employees who have authorized access to an organization's networks and resources.
- Phishing Attacks: Messages or emails that seem to come from a trusted sender but are typically designed to steal user data, financial details, login credentials, or other sensitive business information.
- Distributed Denial of Service (DDoS) Attacks: Attacks that overwhelm networks with excessive traffic from a distributed network of compromised devices (botnet), causing websites and servers to slow down or become completely inaccessible.
- Ransomware Attacks: Malware that locks a victim's data or device and demands a ransom to unlock it, threatening to keep it inaccessible or cause further harm if the payment is not made.
Why Integrate SIEM Tools with MDM Solutions?
Integrating MDM with SIEM tools bridges the gap between device management and security intelligence. This combination offers a comprehensive solution that enables organizations to proactively monitor, detect, and respond to security threats across their mobile ecosystem.
How Do SureMDM and SIEM Tools Work Together?
By integrating SureMDM with SIEM tools like Splunk, LogRhythm, ArcSight, and Coralogix, organizations can ensure that all available log data is continuously monitored for potential threats. When a breach occurs, the log data collected in the SureMDM Console is shared and analyzed by the SIEM tool, enabling security teams to:
- Investigate the Incident: Analyze logs within the SIEM tool to identify the root cause of the breach.
- Identify Additional Compromised Devices: Check if other devices have been affected.
- Take Immediate Action: Implement remediation steps, such as revoking access, isolating compromised systems, or performing a full device wipe.
This is how it looks on your SureMDM Console
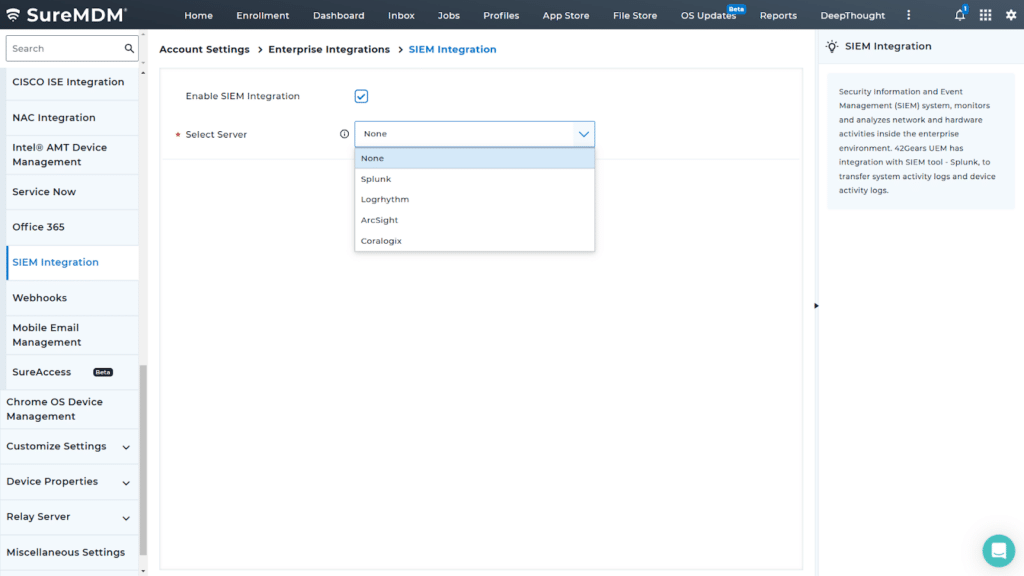
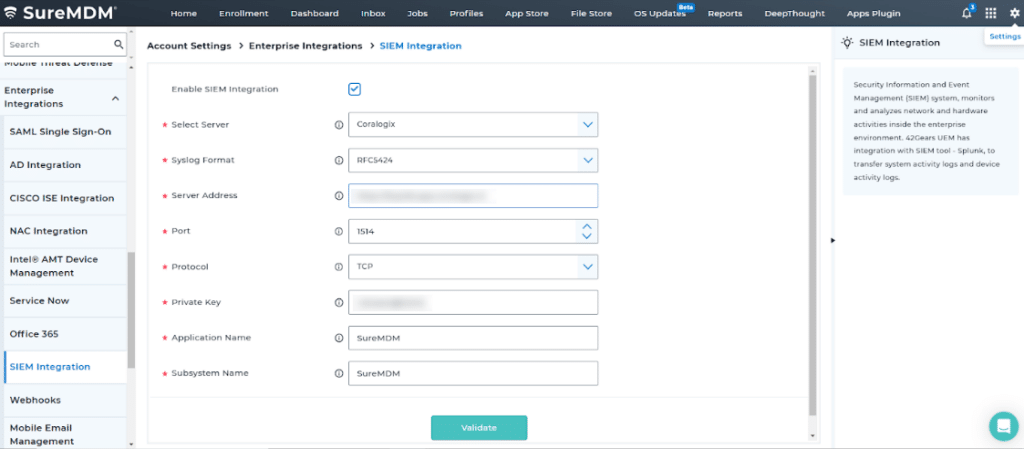
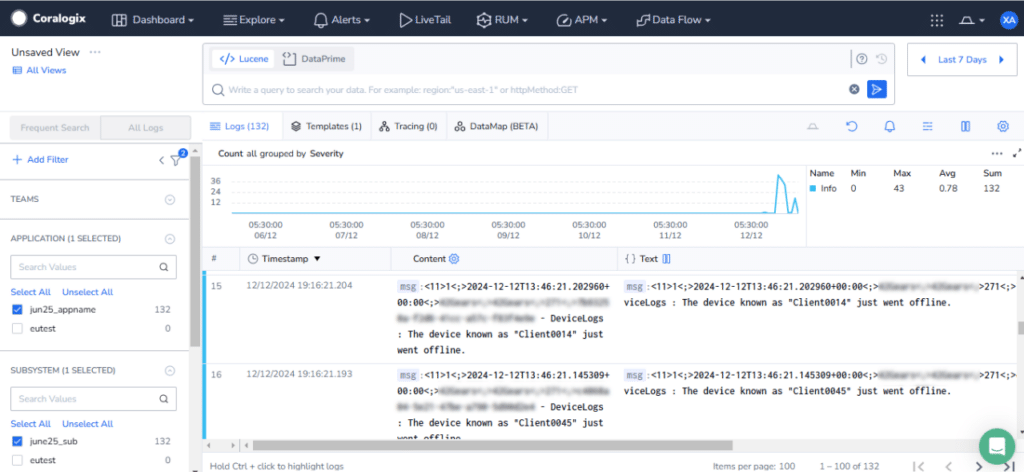
Benefits of SureMDM + SIEM Integration
Integrating SureMDM and SIEM helps organizations achieve a more comprehensive and proactive security posture. This synergy enables you to:
- Proactively Monitor the IT Infrastructure: Continuously monitor the ecosystem for suspicious activity, such as unauthorized device configurations, data breaches, or malware infections.
- Detect and Respond to Threats Faster: Rapidly identify and respond to security incidents by correlating device-specific information with broader network and system events.
- Strengthen Organization’s Security Posture: Enforce strict security policies on mobile devices, such as password complexity, encryption, and remote wipe.
- Reduce the Risk of Data Breaches: Mitigate the risk of data breaches and unauthorized access to sensitive information.
- Pattern-Based Threat Detection Alerts: Set up alerts based on previous patterns to streamline the detection of cyber threats.
Sum It Up
By combining SureMDM and SIEM tools, organizations can create a robust, proactive defense strategy that enhances security, reduces risks, and ensures operational continuity in the face of evolving cyber threats.
Strengthen your threat detection
and mitigation strategies with
SIEM and SureMDM integration
Subscribe for our free newsletter


