Mastering Windows CVE Management: From Detection to Remediation
Ene 10, 2025 | Nareddy Saivikas Reddy
Are you an IT admin managing a fleet of Windows devices in your organization?
If so, then you should be using a Mobile Device Management (MDM) solution to effectively monitor and manage those devices. But here’s the thing: considering the sophistication of cyber-attacks, monitoring and managing the devices alone is no longer enough.
In 2023, over 26,000 vulnerabilities were published1 and cybercriminals are always looking for vulnerabilities to exploit, from phishing attacks to ransomware, and everything in between. As an IT admin, you have a responsibility to not only ensure that devices are updated, configured, and compliant with corporate policies but also safeguard those devices against emerging threats.
One critical aspect of this challenge is managing CVEs (Common Vulnerabilities and Exposures) —a key component of your organization’s security strategy. But what exactly is a CVE, and how do they pose risks to your organization?
What is CVE?
A CVE (Common Vulnerabilities and Exposures) is a publicly disclosed security vulnerability or exposure in an operating system. Each CVE is assigned a unique identifier, such as CVE-2024-12345, which allows it to be tracked and referenced consistently across various security databases and tools.
What Are the Risks Posed by CVEs?
The greatest risk organizations face from CVEs is the potential for exploitation if these vulnerabilities are not promptly addressed. Cybercriminals are constantly scanning for weaknesses in systems, and CVEs provide them with a roadmap to launch attacks.
Did you know? Unpatched vulnerabilities were involved in 60% of data breaches2. That’s not all, here is the list of a few important risks posed by CVEs
- Easy access for malicious actors and hackers
- Theft of sensitive customer data or disruption of critical operations
- Serious security concerns for critical IT infrastructure
- Intellectual property theft that can compromise competitive advantage
- System downtime or data theft that causes financial loss and reputational damage
Worried about the impact of CVEs and looking for a reliable solution to safeguard your devices? The answer to both is 42Gears Mobile Device Management Solution SureMDM
We’re excited to announce a key enhancement to SureMDM: CVE Vulnerability Management, to help organizations tackle the growing challenge of identifying vulnerabilities and applying
CVE Vulnerability Management in SureMDM
Think about it: How much time and effort does your team invest in researching and prioritizing the vulnerabilities?
With hundreds of managed devices, manually researching, prioritizing, and patching vulnerabilities is time-consuming for IT teams. The longer the vulnerability goes unaddressed, the higher the likelihood of a successful attack. And once an exploit occurs, it can lead to devastating consequences.
So, how does SureMDM help address these challenges?
SureMDM CVE Vulnerability Management provides organizations with centralized visibility into vulnerabilities across onboarded devices and offers built-in remediations, enabling IT admins to quickly apply patches and reduce security risks.
How Does CVE Vulnerability Management in SureMDM Work?
To simplify the process of vulnerability management, SureMDM is bundling all security-related features under one umbrella called “Security”, with the “CVE dashboard” rightly placed within it.
- SureMDM consistently retrieves the latest CVE details from the Microsoft Security Response Center (MSRC)
- SureMDM then scans all the enrolled devices against these vulnerabilities
- All the identified vulnerabilities on the devices are listed along with the necessary details
- Admins can choose to remediate all devices for all the CVEs at once or select devices based on test plan requirements or staggered rollout
Get a Complete Picture of Your CVE Vulnerability Management
SureMDM offers a comprehensive CVE dashboard that provides insights on overview of vulnerabilities and their impact on devices. This is how it looks on your console
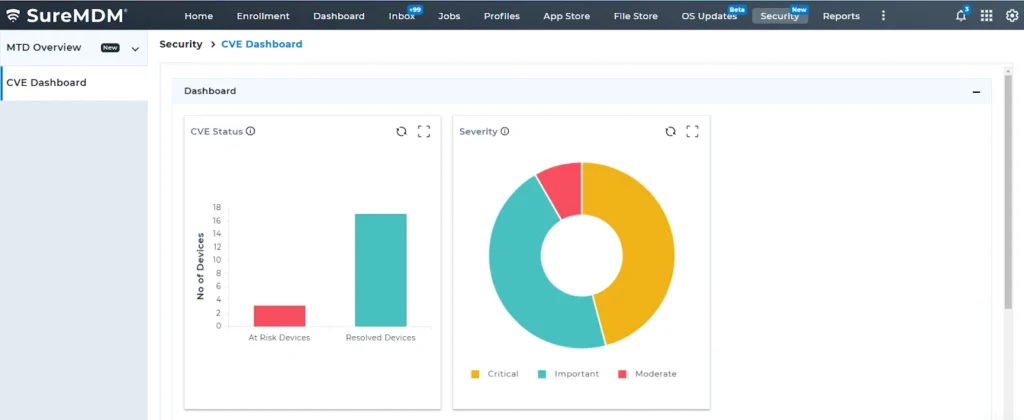
What do these graphs visualize?
- CVE Status Bar Chart
- The chart helps to visualize the current state of device security in an organization
- It provides insight into how many devices are still at risk and how many have been secured or resolved against vulnerabilities
- The comparison between the two bars offers a quick overview of the organization's overall vulnerability management status: a larger "At-Risk" bar indicates more devices need attention, while a larger "Resolved" bar shows good progress in addressing security issues
- Severity Pie Chart
- View the number of devices ‘at-risk’ grouped by vulnerability severity: Critical, Important, Moderate, Low, and None
- The pie chart gives a more granular view of how many devices are exposed to each severity level of vulnerabilities. Admins can click on a segment to drill down into more specific information about the devices affected within that severity category
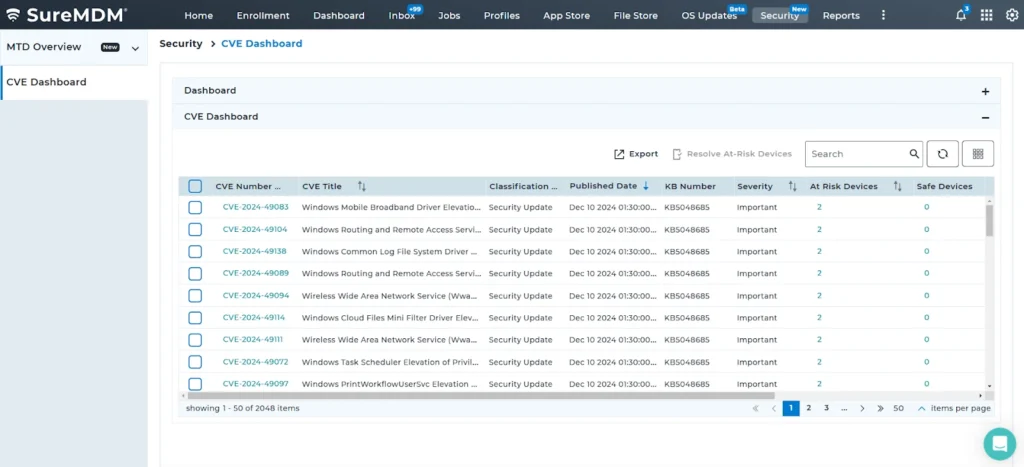
What does this table communicate?
It provides a comprehensive overview of exposed CVEs within an organization, detailing the affected devices along with important information such as the unique identifier, name, classification, published date, related Microsoft KB number, severity level, the count of at-risk devices and safe devices, the need for a reboot, CVSS scores, and the organization that reported the vulnerability.
Benefits of SureMDM CVE Vulnerability Management
- Provides protection against known vulnerabilities
- Reduces response time to emerging threats and patches
- Enhances security visibility across your device fleet
- Simplifies the IT admin’s job of ensuring timely patches for known CVEs
- Minimizes risks and downtime by proactively addressing vulnerabilities before they can be exploited
- Ensures compliance with industry standards and regulatory requirements
- Offers a centralized system to manage vulnerability remediation across your entire mobile fleet from a single dashboard
Note: While applying patches for exposed CVEs helps mitigate risks associated with those specific vulnerabilities, it does not guarantee complete protection against future threats. CVEs are initially reported by Microsoft, and SureMDM simplifies the process of applying these patches across devices (Windows 10 & 11 OS-specific CVE patching). However, ongoing vigilance and additional security measures are required to ensure comprehensive protection against evolving vulnerabilities.
To Sum It Up
A CVE Vulnerability Management system is not an option, but mandatory. Don't let vulnerabilities compromise your organization’s security posture. SureMDM offers reliable CVE Vulnerability Management to safeguard your devices against the risks posed by CVEs. Apart from CVE Vulnerability Management, SureMDM also offers an advanced patch management solution for Windows to ensure timely patching and stay ahead of cyber attacks.
Source
1. Qualys
2. Comparitech
Don’t wait for a breach—
implement CVE management
with SureMDM now!
Subscribe for our free newsletter


