Beyond Root: Sudo Access for Granular Admin Control in Linux Devices Using SureMDM
Okt 29, 2024 | Nareddy Saivikas Reddy
Managing Linux devices that run on different distributions, including Ubuntu, Redhat, Fedora and CentOS, has traditionally been a challenge for system administrators. It gets even more challenging when they have to selectively manage admin privileges to accomplish certain administrative tasks without compromising on device security.
In this blog, let’s understand more on the admin privileges in a Linux environment starting with root user in Linux.
What is a Root User in Linux?
The term ‘root user’ needs no introduction for seasoned sysadmins; for curious newcomers, it is a user account with the highest administrative privileges. A root user account can perform any administrative tasks like adding/removing user accounts, installing/uninstalling applications and files, modifying system settings, etc.
However, any mistake by the root user can be catastrophic, all it takes is a bad command to make the whole system compromised. Whether root users are seen as superheroes or supervillains is determined by their actions and its impact on the organization. It is always a best practice to reserve the root user for administrative purposes only, and use a regular user account for the rest of time.
But what if there is a need to perform the administrative tasks? Is the root user always required to log in for every administrative task? Well, that’s where the sudo command comes in handy.
What is a Sudo User in Linux?
A sudo (short for “superuser do”) user is a regular user who can temporarily gain administrative privileges for specific tasks that are normally reserved for the root user. Sudo access provides a more secure way to perform administrative tasks compared to directly using the root user.
Sudo Management in SureMDM
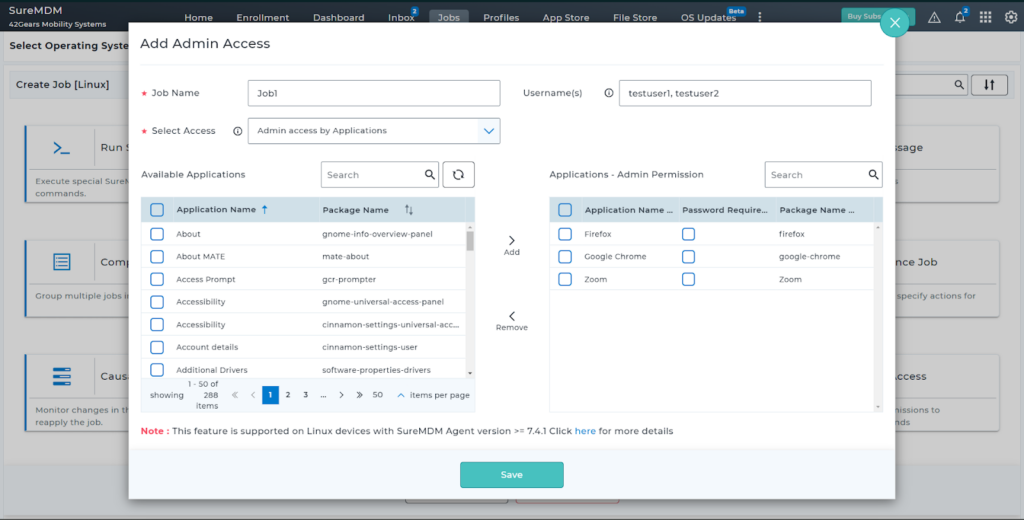
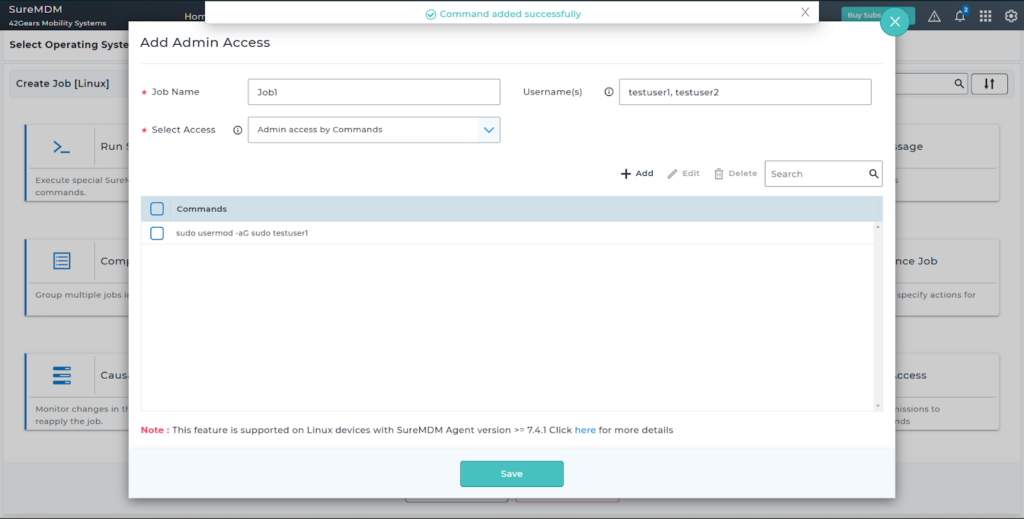
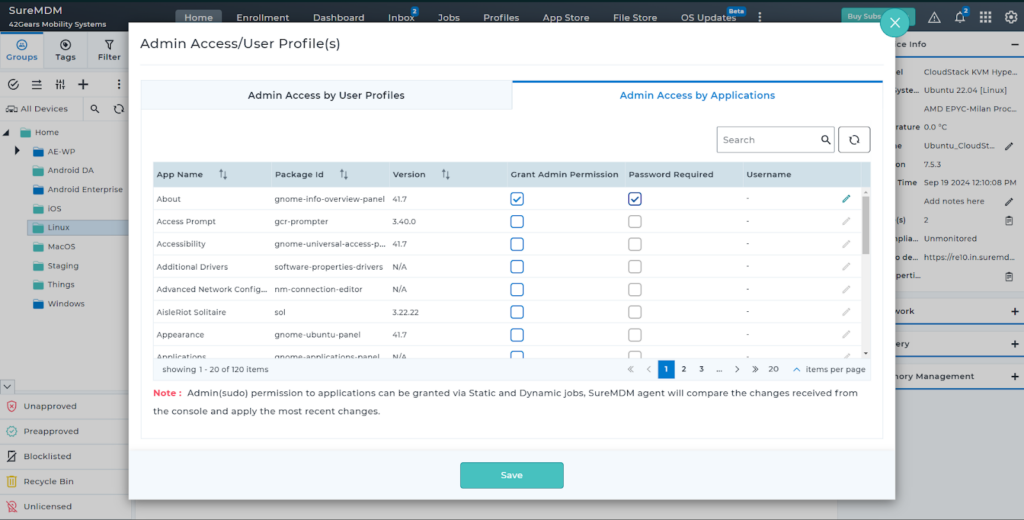
SureMDM supports granting administrative access for user accounts, allowing users to perform tasks like installing applications, modifying files, and managing device configurations, etc. To serve the evolving requirements of our customers, SureMDM now extends sudo access to specific applications along with commands (we call it ‘Admin Access’ in SureMDM).
It just takes five simple steps for sysadmins to manage sudo access in SureMDM:
- Create a policy (Jobs in SureMDM) to allow Admin Access to certain applications and commands.
- Deploy the policy on required devices.
- Sysadmins can also grant Admin Access to a group of devices.
- Once done, to revoke the Admin Access, just modify the policy to required configuration and redeploy it to the devices.
- Track all the Admin Access permissions on all devices using reports.
To grant admin access for a single device, sysadmins can leverage device grid using policies (Dynamic Job in SureMDM).
Let’s say a system administrator needs to clear disk space from restricted folders. Doing this can be tricky because modifying or deleting files in these folders typically requires elevated permissions. Without sudo access, the administrator would need to log in as the root user, which poses a higher risk of accidental damage due to the unrestricted privileges of the root account.
To mitigate this risk, the administrator can grant admin (sudo) privileges for specific tasks to a regular user. This approach allows the regular user to clear disk space from restricted folders without needing full root access. By doing so, the system administrator reduces the risk of human error and potential damage associated with direct root access.
This is how Admin Access feature looks on your console
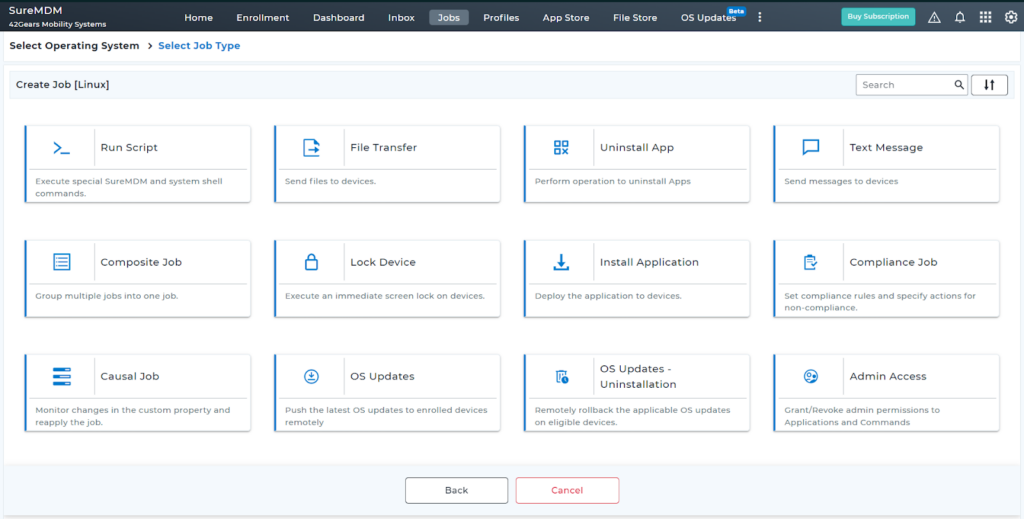
Linux distributions that SureMDM supports:






Benefits of Sudo Management using SureMDM
Reduced Risk Surface Area:
By limiting administrative privileges to specific commands and applications, sudo minimizes the risk of accidental or malicious damage.Granular Control Over Tasks:
Sudo offers precise control allowing only necessary performance with elevated privileges, reducing overall security risks.Ease of Use:
Users can perform administrative tasks without needing to switch/login to the root account, simplifying workflows.User Account Report:
Get insights on how many users have sudo access at the whole organizational level making it easy for tracking the permissions.Alignment with Zero Trust Principles:
Sudo access grants administrative privileges to only what is required, further aligning with Zero Trust principles.
Conclusion
While powerful, leveraging a root user account to make administrative changes poses risks due to its extensive privileges, and using it for every administrative action can lead to potential system compromises. Sudo Management in SureMDM helps the system administrators to streamline administrative tasks by limiting elevated privileges to necessary actions only. SureMDM reporting capabilities allow for easy tracking of sudo permissions across all devices, making it a comprehensive solution for managing Linux administrative tasks securely and efficiently.
Enhance Linux device security and
streamline admin tasks with
SureMDM sudo management
Subscribe for our free newsletter