The Evolution of Secure Communication: From Hieroglyphics to ZTNA
Nov 21, 2024 | Prakash Gupta
In the realm of cybersecurity, a new paradigm is transforming how we approach secure access to business resources: Zero Trust Network Access (ZTNA). But to truly appreciate the significance of this technology, let's embark on a journey through time, exploring how humans have safeguarded their most precious information throughout history.
Origin of Secure Communications
Imagine yourself in ancient Egypt, 3000 BCE. A pharaoh needs to send a confidential message to his general on the battlefield. How does he ensure the message remains a secret? The solution: hieroglyphics known only to a select few. This early form of encryption marks the birth of secure communication.
Fast forward to 500 BCE in ancient Greece. The Spartan military employs the "scytale" - a cylinder wrapped with a strip of parchment. Messages written on the unwrapped parchment appear as gibberish, decipherable only when wrapped around a cylinder of the correct diameter. Here, we see the concept of "shared secrets" emerging - a precursor to modern encryption keys.
In the Middle Ages - Smoke Signals to Sealed Letters
As civilizations grew more complex, so did their methods of secure communication. In medieval Europe, castle towers served as vantage points for smoke signal communications - a rudimentary form of network that relied on line-of-sight security.
By the Renaissance, special wax seals on letters became the standard for ensuring message integrity and sender authentication. Breaking the seal would be a medieval data breach!
The Modern Digital Age
As we enter the era of digital communication, the need for secure access to resources becomes increasingly critical. Let's explore the evolution of secure access technologies:
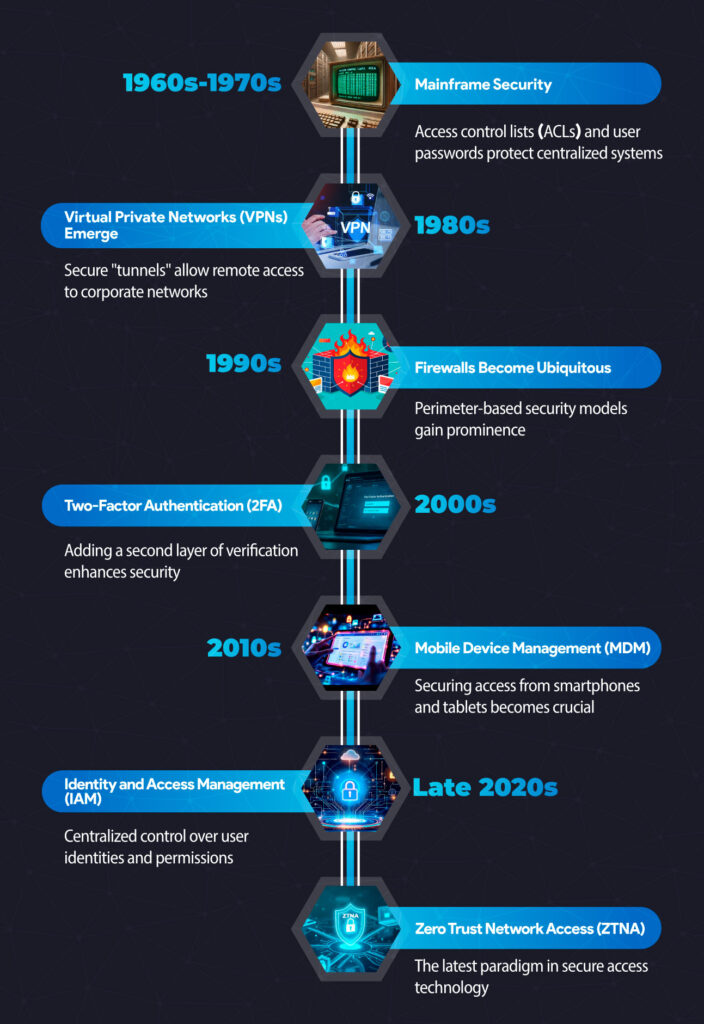
ZTNA: The Innovation in Secure Access
So, what makes Zero Trust Network Access the latest and greatest in this long lineage of secure communication technologies?
ZTNA embodies a fundamental shift in security philosophy: "never trust, always verify." Unlike traditional perimeter-based security models, ZTNA assumes that no user, device, or network should be trusted by default, even if they're already inside the corporate network.
Key principles of ZTNA include:
- Continuous authentication and authorization
- Least privilege access
- Micro-segmentation of resources
- Device posture checking
- Encryption of all traffic
Imagine a medieval castle where, instead of relying solely on the strength of its outer walls, every room, hallway, and treasure chest requires separate verification. That's ZTNA in action.
In practice, ZTNA might look like this: A marketing executive working from a café needs to access sensitive customer data.
With ZTNA:
- Her identity is verified (not just her password, but potentially biometrics or behavioral patterns)
- Her device's security posture is checked
- The network she's on is analyzed for potential threats
- She's granted access only to the specific data she needs, nothing more
- Her session is continuously monitored for anomalies
This granular, dynamic approach to security is what sets ZTNA apart from its predecessors. It's not just about keeping the bad guys out; it's about ensuring that even those inside the system can only access what they absolutely need.
As we face an increasingly complex threat landscape, with remote work becoming the norm and cloud services proliferating, ZTNA represents a paradigm shift in how we approach security. It's the latest chapter in humanity's ongoing quest to protect our most valuable information - a quest that began with hieroglyphics and smoke signals, and now continues in the digital realm.
The pharaohs of ancient Egypt could scarcely have imagined a world where information travels at the speed of light across global networks. Yet, the fundamental need to secure that information remains unchanged. ZTNA is our modern answer to this age-old challenge, providing a level of security and flexibility that our ancestors could only dream of.
As we look to the future, one thing is certain: the evolution of secure communication is far from over. ZTNA is just the latest milestone in this fascinating journey - and who knows what groundbreaking technologies the next chapter will bring?
Never Trust, Always Verify
Secure Access to Corporate
Resources with ZTNA
Subscribe for our free newsletter








